A gift from a brother-in-law I haven’t seen in five years: a bricked backup drive which, as the resident IT pro, I must spend my afternoon recovering. Apparently I agreed to this on the phone about a year ago.
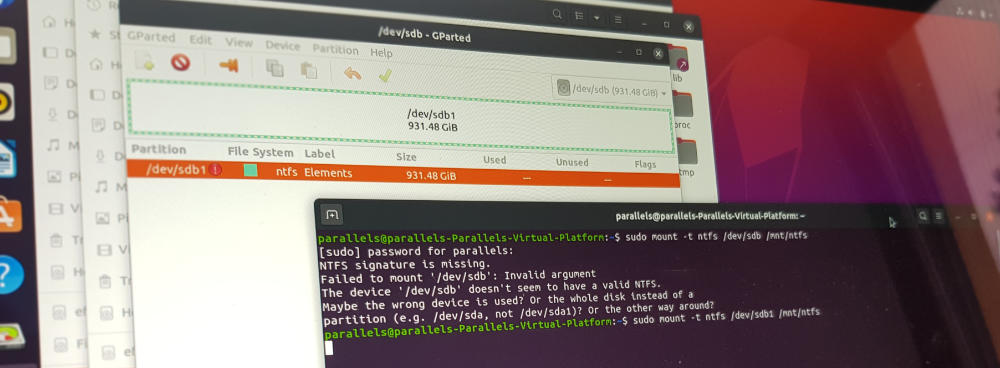
The good news: I’ve managed to mount it and views the files. The bad news: I don’t have enough disk space on my laptop to recover his files, and definitely don’t have enough data to upload it to the cloud. So, a partial victory.
Oh, and did I mention? Yep, the drive is stuffed with malware, an executable in every single directory on the drive. Enter a hastily downloaded Ubuntu VM (virtual machine), capable of both reading and writing to a NTFS disk, and a manual purge of every single exe file on the disk, legitimate or not.
Yeah, so sorry, your dodgy cracked version of Office 2010 — probably one of the sources of the malware in the first place — is gone, along with WinAmp, WinRar and all that other long-redundant software. But hopefully, all of their photos, videos, documents and music remain intact. Hopefully they will now be able top open the drive on a Windows computer without it triggering armageddon — unfortunately we don’t have one to hand, with which to test.
As for the digital hygiene they will need to practice going forward: that one’s going to be more tricky. Alas, their generation haven’t heard of OpenOffice (which I hate) or OnlyOffice (which is pretty great), so will continue trying to download pirate-software soaked in virulent malware. And unfortunately my interpretation layer — my wife — will probably not convey my technical advice precisely, but will filter it through her understanding of what I said, which is not always the same thing.
So my work, I hope, is done, five hours later. Until next time.
Last modified: 14 August 2022
